Let's go shopping on the dark web.
- Insider threat.
- The dark web.
- Ransomware.
- Consequences.




The first step has been taken. Now you're going to learn the ins and outs of various (spear) phishing techniques. You are now stepping into the role of perpetrator yourself. Hopefully you are ready to betray your colleagues...
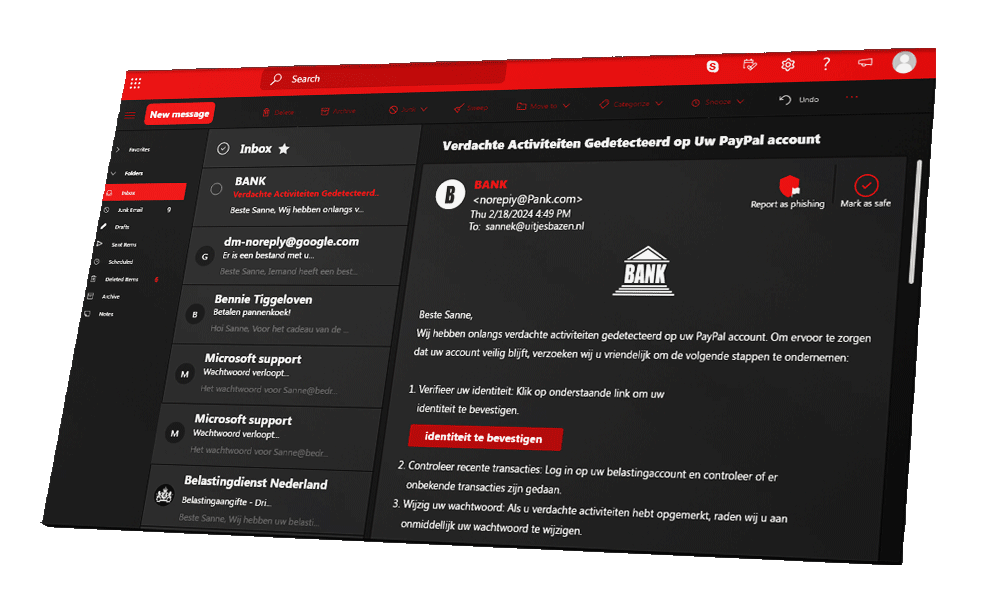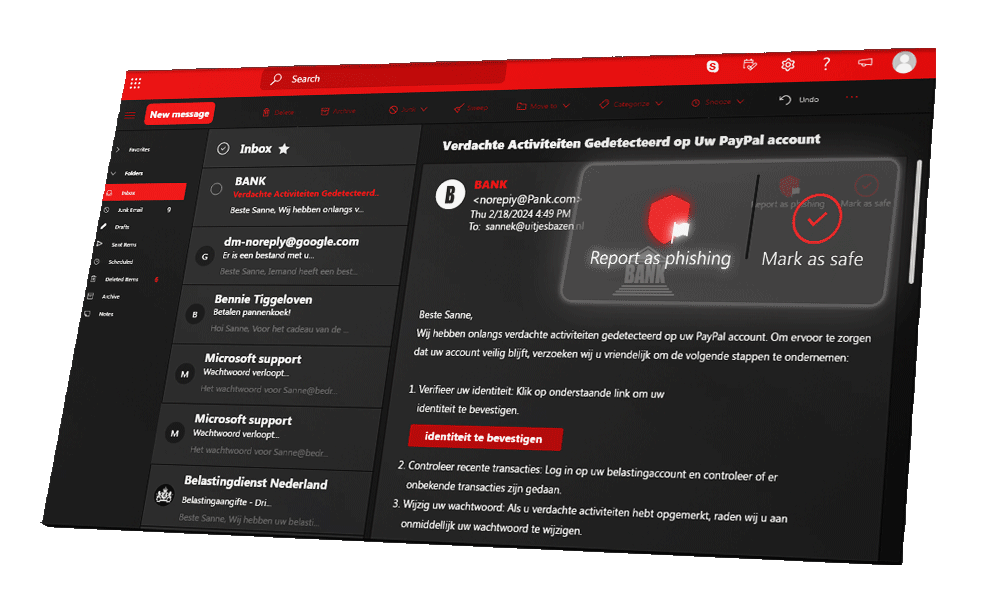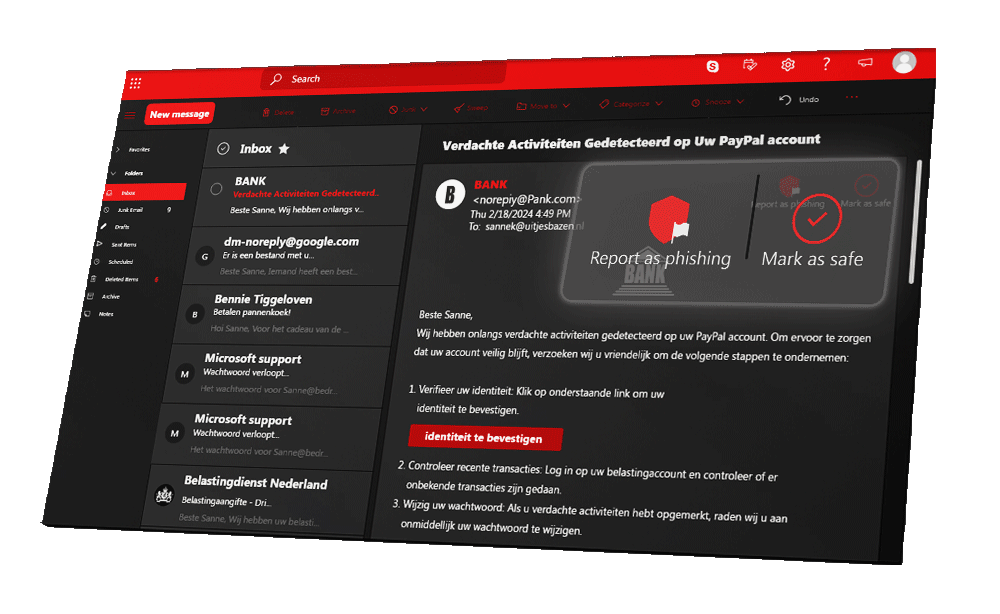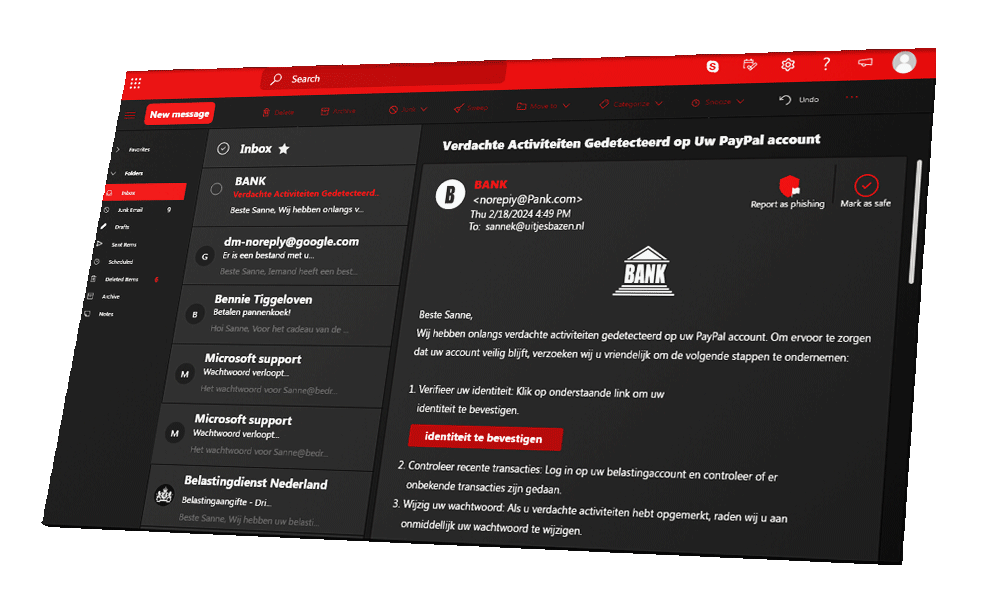
Hidden URLs, suspicious attachments, spelling mistakes, weird links and asking for your personal information. Phishing is perhaps the best-known form of cybercrime.
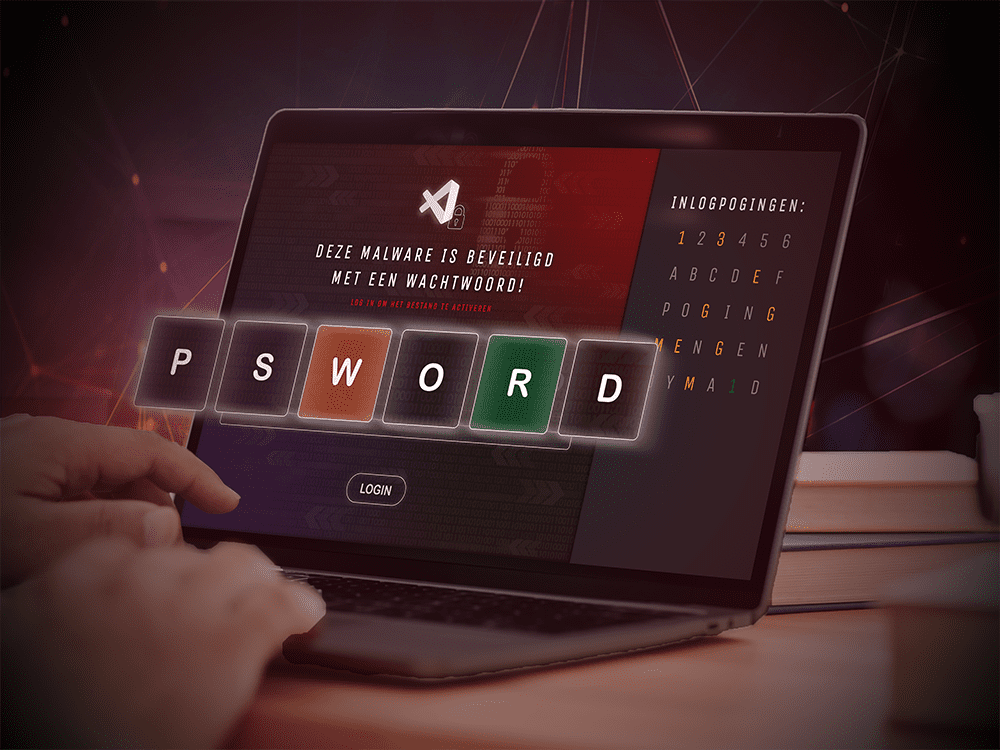
What are the most common passwords, which passwords are the most difficult to crack and how easy is it for a hacker to crack a password?
Practice makes perfect. Time to put your skills into practice. Prepare malware to disrupt your company's network. Translate the binary code to see what letters the numbers consist of and complete the code further.
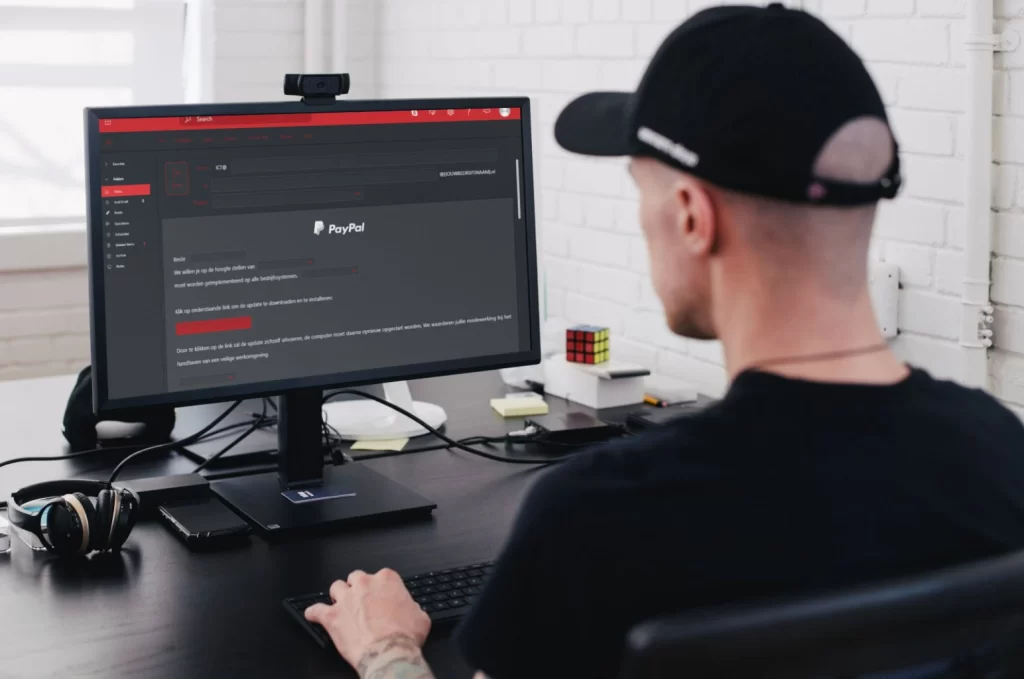
Ready to really betray your colleagues? Good, because now you can't go back. You're going to use what you've learned to create a spearphishing email to frame your colleagues. Do you know how to choose the right options to make the phishing email as realistic as possible?
PhantomX's dark plan is unfolding. Are you ready to spread malware?
We promise that the button below will lead to "request a demo." However, in the future, you will think 3 times before clicking just any button.
Request a free demo now