Examples, species and protection
Cybercrime is a rapidly growing problem in our digital society. It includes all kinds of illegal activities using various attack techniques. Social engineering, the Internet, physical accesses and bank fraud are just a few examples. In this blog, we will discuss some examples of cybercrime, different types of cybercrime and how we can guard and protect against it.
1. Phishing
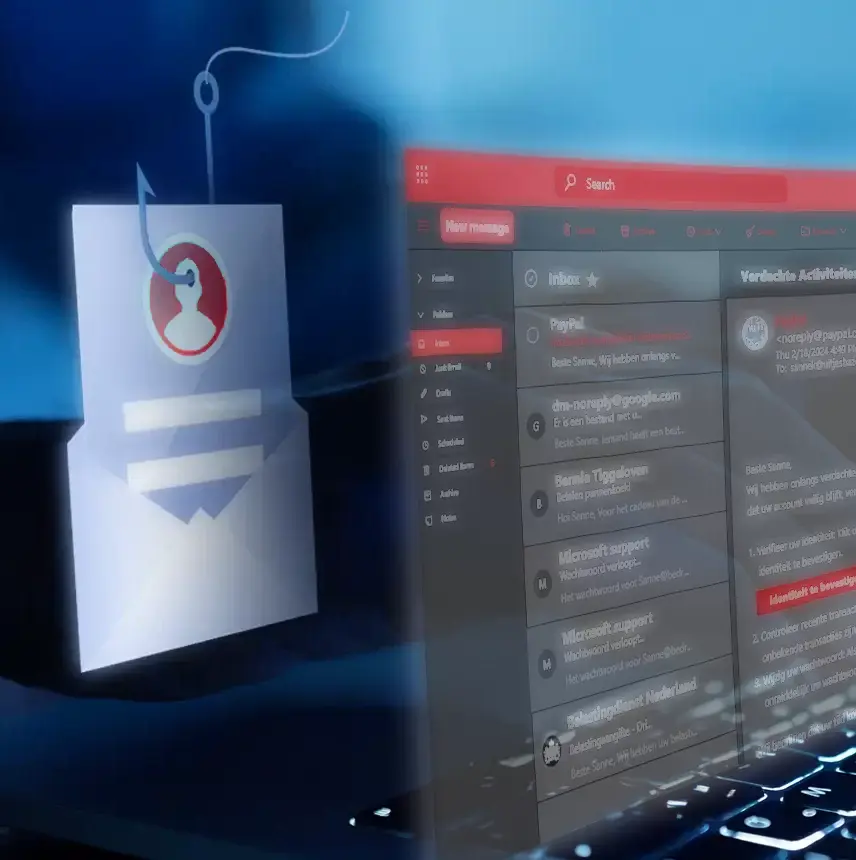
In phishing, cybercriminals use fake emails or text messages to try to obtain, among other things, confidential identity information and the security codes for Internet banking, mobile banking and payment cards. In doing so, criminals try to appear reliable (for example, from a well-known organization, such as a bank). By obtaining the data, cybercriminals gain direct access to the victim's bank account.
For example, the cybercriminal can use a copy of the passport to take out loans, order subscriptions or even rent homes at the victim's expense. It also happens that a criminal keeps the data for a while, only to strike later unexpectedly.
2. Spear phishing
With spear phishing, criminals go one step further. Here, criminals focus specifically on a person. To make the phishing appear as credible as possible, information about this person is gathered through social media, news articles or other websites that feature this person.
A phish message is then constructed with recognizable things collected about the victim (for example, that vacation in Ibiza, or that completed English study). With this data, the credibility of a phishing email is greatly increased, and the victim is more likely to fill out data or make payments.
3. CEO fraud
CEO or CFO fraud involves someone else pretending to be the CEO or CFO in order to abuse their authority to force false payments or send sensitive information.
Employees are most likely to react when the authority of the CEO/CFO is abused. The more time and effort a criminal spends on CEO fraud, the more likely he is to succeed in receiving payments or information.

4. Ransomware
This is a type of malware that encrypts files on your computer and demands a ransom to release them again.
Malware is any software used to disrupt computer systems, collect sensitive information or gain access to private computer systems.
5. Identity Fraud
In this process, criminals use stolen personal information to impersonate someone else, such as to take out loans or make purchases.
Think: opening a bank account with your stolen passport. Or renting a car with your lost driver's license, only to never return that car.


6. Hacking and online bullying
Cybercriminals break into computer systems to steal sensitive information, take down websites or cause damage.
This includes threats, stalking and shame sexting through social media and other online platforms.
Types of cybercrime
- Business Email Compromise (BEC): criminals send fake emails on behalf of a company to commit financial fraud.
- DDoS attacks: this involves overloading a website or network with traffic, making it inaccessible.
- Exploitation of vulnerabilities: criminals exploit weaknesses in software to gain access to systems.
- Reuse passwords: if you use the same password for multiple accounts, criminals can easily access all your data.

Recent examples of cybercrime
Security.com
Security.com
NOS
Now.com
Recognize and protect
- Be aware of the dangers and be alert: Employee awareness will reduce the chances of being tricked into CEO fraud or opening suspicious emails and clicking on links and attachments.
- Use strong passwords: unique and different passwords or passphrases for each account.
- Install security software: make sure you have good antivirus and anti-malware programs.
- Stay informed: follow news about cyber threats and adjust your security measures.
- If something seems too good to be true, it often is! Imagine yourself: you receive an e-mail from your uncle from America (which you did not know existed). It indicates that you are his sole heir. A sizable inheritance is therefore waiting for you. All you have to do is answer the e-mail with your name and bank account number. That sounds too good to be true, right....


For whom.
This game is designed for employees regardless of their level of experience with cybersecurity. It can be used during a kick-off cybersecurity awareness campaign, when onboarding new employees, to build support for the fight against cybercrime or as a group activity.
By learning through play, employees build the skills needed to strengthen the digital front line and protect the organization from the ever-changing threats of cybercrime.